After a string of high-profile hacking incidents, Twitter has finally introduced a two-factor authentication system as a way for members to keep their accounts more secure.
On Wednesday, the information network rolled out the new login verification feature, which people can select to require entry of a six-digit code, in addition to their standard password, to gain access to their Twitter accounts.
"When you sign in to twitter.com, there's a second check to make sure it's really you," the company said in a blog post announcing the optional security feature.
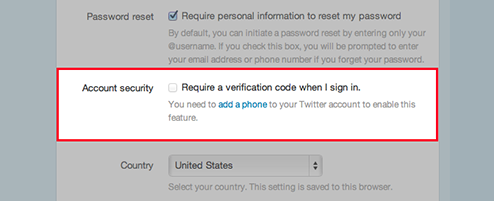
The two-factor system mirrors that of Facebook's and requires members to provide a phone number to which Twitter can send a unique code with each login attempt. Twitter users can turn on two-factor authentication from their Account Settings page, where they can tick the box to "Require a verification code when I sign in." Users then need to enter their phone number, and Twitter will subsequently text the number for verification purposes.
"With login verification enabled, your existing applications will continue to work without disruption," Twitter said. "If you need to sign in to your Twitter account on other devices or apps, visit your applications page to generate a temporary password to log in and authorize that application."
The additional security measure certainly complicates the login process, but the extra step is one many Twitter users, particularly brand users, will welcome with open arms. Last month, the Twitter accounts of CBS News' programs "60 Minutes" and "48 Hours" were compromised by hackers. (Disclosure: CNET is a unit of CBS Interactive.) The Associated Press was also the victim of a particularly cringeworthy breach when hackers sent out a false tweet that claimed the White House had been bombed. This news caused an immediate dive in the stock market.
Two-factor authentication should help Twitter defend against hacking attempts and partly repair its reputation as a public square for people, businesses, and celebrities.
Source: CNET


